Cylance
Introduction
The Cylance Tasks provides essential functionalities to interact with the Cylance endpoint security platform. The task enables users to perform actions such as listing threats, exploding threats, and retrieving device information. To utilize the Cylance task, ensure that the necessary Cylance connector is configured.
Configuration
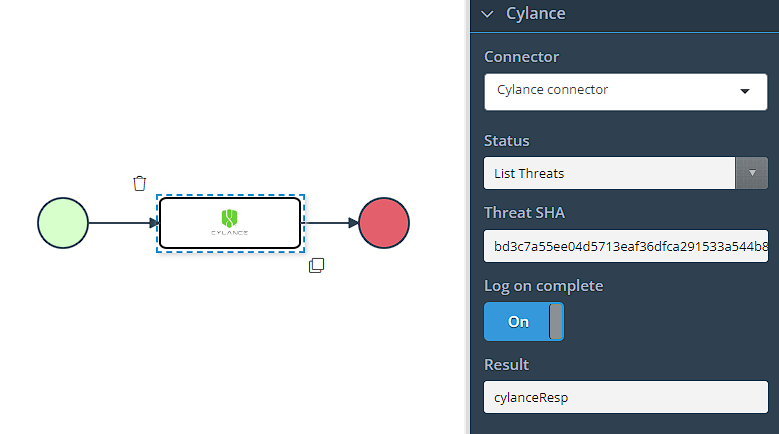
Connector- Previously configured Cylance connector.Status:List Threats- Retrieve a list of threats detected by the Cylance.Explode Threat- Detailed information about specific threats detected by Cylance.Get Devices- Retrieve device information from the Cylance platform.
Threat SHA- Threat's Secure Hash Algorithm.Log on complete- Prints the response in the case log.Result- The response received from the Cylance platform.